For years, traditional IT security was built on a simple assumption: if you were inside the network, you could be trusted. Firewalls kept the bad guys out, and anyone who made it past those defenses was treated as safe.
But the world has changed.
Today, employees work remotely. Applications run in the cloud. Vendors connect to your systems. And cybercriminals use artificial intelligence (AI) to launch smarter, faster attacks from anywhere.
That’s why more and more businesses are shifting to a new cybersecurity model: Zero Trust Security.
So, what is Zero Trust Security? This post will explain what Zero Trust Security is, why it matters, and how you can begin applying its principles without needing to be a tech expert.
What Is Zero Trust Security?
Zero Trust Security is a modern cybersecurity strategy based on one key idea: never trust, always verify.
In the old model, once someone got inside your network, either physically or through a VPN, they were generally trusted to access data and systems. But with Zero Trust, no one gets a free pass. Every user, every device, every app must prove who they are, every time.
This framework assumes that threats can come from both outside and inside your organization, so every access request is treated as potentially risky until proven otherwise.
“Think of your business like an airport,” says Grant Eckstrom, vCISO at Succurri.
“Even if you work there, you still need to go through security, show ID, and scan your bag every day. That’s Zero Trust in plain English. It doesn’t matter if you’re a pilot or a passenger—you don’t get through without verification.”
What Is Zero Trust Model & Why the Old Model No Longer Works
The “castle and moat” security approach (build a wall, trust everyone inside) made sense when businesses had on-site servers, office-only workforces, and limited internet exposure.
But those days are gone. Today:
- Employees access systems from home, airports, or client sites.
- Businesses rely on SaaS tools and cloud infrastructure.
- Cybercriminals use phishing, ransomware, and AI tools to bypass old defenses.
- Supply chain and vendor access introduce new vulnerabilities.
In this environment, trust is a risk, and Zero Trust is the answer.

Core Principles of Zero Trust Security
So, if you’ve been researching “what is zero trust cyber security”, the answer isn’t as black and white as it may seem. Zero Trust isn’t a single product. It’s a comprehensive approach that uses multiple technologies and policies to continuously verify and protect your business environment.
Here are the key components:
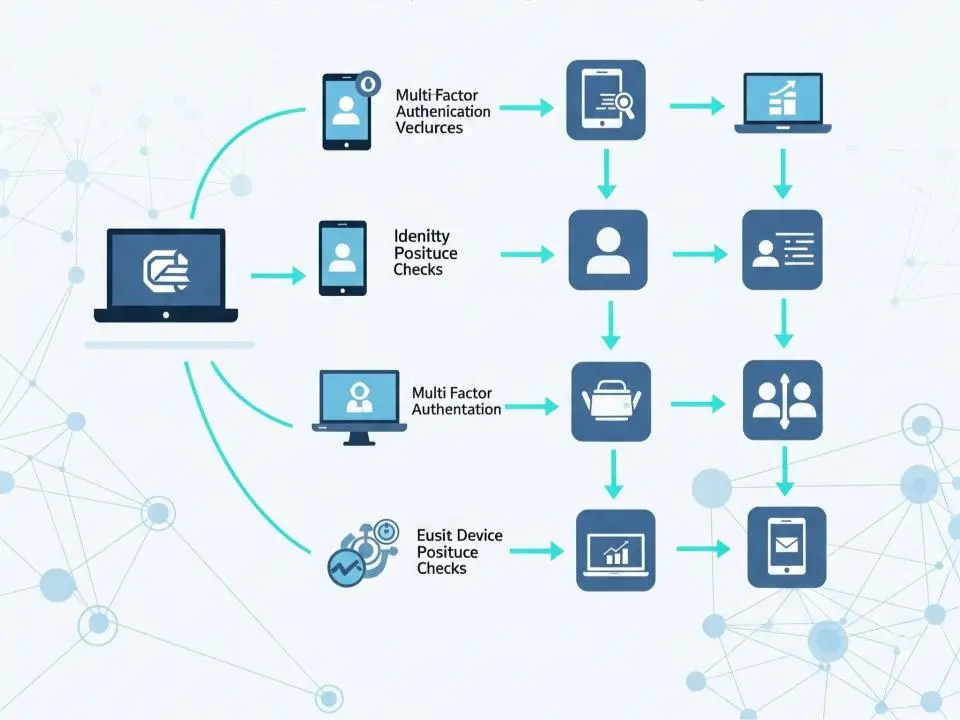
1. Strong Identity and Access Management (IAM)
Every user has a unique identity that determines what they can do and see. With Zero Trust, users must log in securely and only get access to what they truly need.
2. Multi-Factor Authentication (MFA)
Passwords alone aren’t enough. MFA adds a second layer of protection, like a text message code or an authentication app, to confirm a user’s identity.
3. Continuous Device Monitoring
Just because a user was verified this morning doesn’t mean their device is still safe. Zero Trust monitors for risky behavior, software vulnerabilities, and signs of compromise.
4. Network Segmentation
Instead of one big open network, Zero Trust divides your environment into smaller, secure zones. That way, if one area is breached, the damage is limited.
5. Least-Privilege Access Controls
Users and systems are given only the access they need, nothing more. This helps prevent misuse, accidental exposure, or a cybercriminal gaining broad access.
6. Endpoint Security
Every laptop, phone, or tablet that connects to your network must be protected. Zero Trust ensures that all endpoints are secure and compliant before they’re allowed to connect.
7. Real-Time Analytics and Behavior Monitoring
Zero Trust uses data to spot unusual behavior, like a user logging in from two locations at once or trying to access files they shouldn’t. These red flags trigger alerts or automatic blocks.
Want a practical way to get started? Download our Business Network Security Checklist for simple, actionable steps.

What Does Zero Trust Look Like in Action?
Let’s say one of your sales reps logs in from their home office to access client proposals. With Zero Trust in place:
- The system checks that it’s really them (via MFA).
- Their laptop is scanned to ensure it has the latest security updates.
- They’re only given access to sales folders, not HR or financial data.
- If they try to access something outside of their role, the system blocks it and alerts IT.
- If their account is accessed from a suspicious IP address later that day, it’s flagged as a potential threat, even if the password was correct.
This continuous, automated monitoring is what keeps your business safe, even when your people, systems, and data are everywhere.
Is Zero Trust Only for Big Businesses?
Absolutely not.
While large enterprises were early adopters, small and mid-sized businesses are now among the most common targets of cyberattacks and the most vulnerable.
Zero Trust can (and should) be implemented at any scale, and many of its core components, like MFA, device management, and user role policies, are easy to implement with the right guidance.
Succurri helps companies of all sizes build Zero Trust into their cybersecurity strategy without disrupting daily operations.
How Succurri Helps You Implement Zero Trust
At Succurri, we work with business owners and IT leaders to:
- Assess your current security environment
- Identify gaps in access control, device protection, and user behavior monitoring
- Create a roadmap to implement Zero Trust components over time
- Manage and monitor your environment so it stays secure, even as your business grows
Whether you’re just getting started with cybersecurity or need help passing an audit, Zero Trust gives you a future-proof framework to reduce risk and protect your business.
Get a Free IT Audit to assess your readiness

Final Thoughts: Zero Trust Is Smart Business
Cybersecurity isn’t just a technology issue anymore; it’s a business survival issue.
Zero Trust Security helps you move beyond outdated assumptions and take proactive control of your digital environment. It protects your data, your clients, your reputation, and your future.
And with cybercriminals using AI to move faster and smarter, this framework ensures your business doesn’t fall behind or become a victim.
“Zero Trust isn’t about paranoia—it’s about preparation. You wouldn’t leave your office unlocked overnight, so why leave your systems unguarded online?”
— Grant Eckstrom, vCISO at Succurri
For more information about our IT services, contact us today.
Related Resources from Succurri:
Business Network Security Checklist
Cybersecurity Services
Free IT Audit
Webinar: Weaponized AI and Its Impact on Business Security